 Banking Trojans and ransomware dominated the malware landscape while compromised business email gained speed according to Sunnyvale, Calif.-based security firm Proofpoint's analysis of first quarter 2016 threats and trends.
Banking Trojans and ransomware dominated the malware landscape while compromised business email gained speed according to Sunnyvale, Calif.-based security firm Proofpoint's analysis of first quarter 2016 threats and trends.
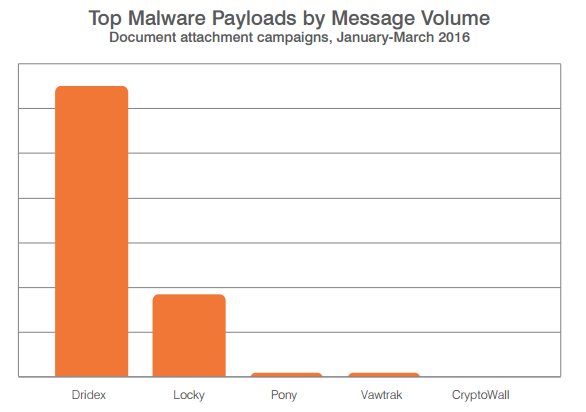
In Proofpoint's “Quarterly Threat Summary,” researchers also revealed ransomware vaulted into the top ranks of the most preferred malware by cybercriminals. Nearly one-quarter of document attachment-based email attacks in the first quarter featured the new Locky ransomware.
“The massive email message volumes associated with Dridex banking Trojan malware gave way to our discovery of the new Locky ransomware,” the report revealed.
The Locky ransomware strain is spreading to victims' systems rapidly. Forbes claimed Locky infects approximately 90,000 systems per day and typically asks users for 0.5-1 Bitcoin (or $420) to unlock their systems.
Proofpoint researchers said Dridex, accounting for 74% of total message volume, was the only malware payload used more frequently than Locky. Other payloads appeared mostly in short bursts. Nymaim entered the top 10, and Vawtrak remained a frequent alternative to Dridex.
“Ransomware is back in a big way with new variants and techniques emerging regularly. Organizations need defenses that can stop these attacks before they can encrypt data and take critical systems offline,” the report said.
More C-level employees are at risk of targeted messages with business email compromise on the rise. Attackers have used more social engineering to persuade users to complete tasks or run malware, as solutions that detect non-malware-based threats like imposter email prevent costly mistakes and breaches.
Some key takeaways from Proofpoint's Q1 2016 research include:
- Impostor email threats, aka business email compromise, are increasingly mature and differentiated. Three-quarters of these phishing attacks rely on fake “reply-to” spoofing to trick users into believing messages are authentic.
- Email continues to be the top threat vector, with malicious message Q1 2016 volume increasing by 66% over Q4 2015, and more than 800% over the same period in 2015. “Email represents the first line of attack for advanced threats and targeted attacks. It serves as a beachhead from which threat actors can pursue further malicious activities,” researchers pointed out.
- Java and Flash Player vulnerabilities continue to pay dividends for cybercriminals as Angler was the most used exploit kit, accounting for 60% of total exploit kit traffic. Neutrino and RIG exploit kit use was also up with an 86% and 136% increase, respectively.
- Every major brand examined increased social media content by at least 30%. As fan- and brand-generated content volumes increase, higher risk follows. The constant challenge for organizations is to protect their brand reputation. “If those interactions are muddled by spam, pornography, and adult language, customers walk away. Brands struggle to manage their social channels. Many also risk costly compliance violations,” the report said.
- Ninety-eight percent of all malicious mobile apps examined in Q1 2016 targeted Android devices, despite the high-profile discovery of an iOS Trojan and presence of risky iOS apps and rogue app stores.
“Threat actors employ a variety of highly effective lures that target departments (such as human resources and accounting) and specific people,” the report disclosed. “These lures use a variety of mechanisms to convince users that attackers' requests for information or money transfers are legitimate.”
© Touchpoint Markets, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more inforrmation visit Asset & Logo Licensing.







