How did a hybrid Trojan steal $4 million from two dozen U.S. and Canadian financial institutions within days?
The GozNym hybrid, part banking Trojan and part ransomware, combines features of Nymaim and Gozi ISFB malware to create a powerful Trojan, IBM Executive Security Advisor Limor Kessem said in an IBM alert. GozNym worked like a double-headed beast, where the two codes relied on one another to carry out the malware's internal operations, he said.
In terms of the Trojan's targets, IBM X-Force Research, which uncovered the hybrid malware, noted the GozNym hybrid's configuration targeted U.S. banks, credit unions and popular e-commerce platforms. Two Canadian financial institutions were also on the list.
“The new GozNym Trojan is the combination of Nymaim and Gozi, a previous version of Vawtrak, also currently used to attack banks,” Pablo de la Riva Ferrezuelo, CTO and founder of buguroo, a threat intelligence startup spun out of Deloitte's European Security Operations Center, said. “Though the combination creates a new malware with evolutions in some of the techniques, it still has something in common: Dynamic web injects in the end user browser.”
De la Riva Ferrezuelo provided an overview of how the hybrid malware works.
1. Typically, a user receives a spear phishing email with a Word document attached. Real case examples are shown below.
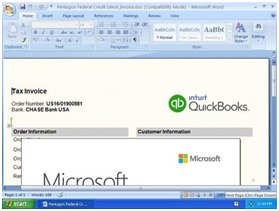
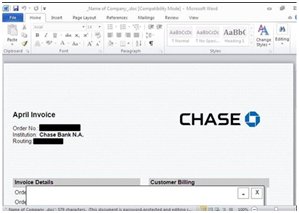
2. The attacker attempts to fool the user by saying that the document was created in an older version and asking them to accept it. Once the user clicks, this enables the macros, which executes a VBScript (a version of Microsoft's Visual Basic programming language) that downloads the dropper. Nymaim, first uncovered in 2013, is a dropper, mainly employed to install other malware, usually ransomware, once it has infiltrated a PC via a browser-based attack.
3. Once the dropper is working, Nymaim can download the other pieces, in this case, the Gozi ISFB.
“One of the new tricks here is that this specific campaign has a modification of the Nymaim malware that is only using the web injects piece instead of the full capabilities; this stops some antivirus solutions from detecting it like before,” de la Riva Ferrezuelo said. This has been happening since the end of last year, when GozNym started to be distributed.
4. When the Gozi ISFB is running, dynamic web injects interact with the user browser, adding additional fraudulent contents.
5. Depending on the campaign, the new attack content can include capturing additional user information, like a second authentication factor. In this example, the criminals have the credentials, so they usually sell them on the black market. After that, other criminals use that data to move money into mule accounts.
“Most commonly, the malware guides the user to stop a fraudulent transaction, but what it's really doing is launching a real fraudulent transaction to a mule account. This is one of the most common ways to move the money,” the buguroo CTO explained.
6. A dedicated team updates and changes the mule accounts continuously.
“These people are not involved with the malware attacks and only work on making sure these accounts are available to the hackers, using fake names and addresses,” De la Riva Ferrezuelo pointed out. This guarantees that accounts are available when needed and ensures no traceability is possible when security analysts attempt to follow and recover the money and identify the attackers.
De la Riva Ferrezuelo said online fraud detection solutions could help credit unions. However, some of the less advanced solutions only focus on signatures or basics patterns and can only protect against already-known Trojans based on old-fashioned techniques.
“GozNym is a perfect example of why financial institutions need technologies that can stop even zero-day malware,” he added.
© Touchpoint Markets, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more inforrmation visit Asset & Logo Licensing.







