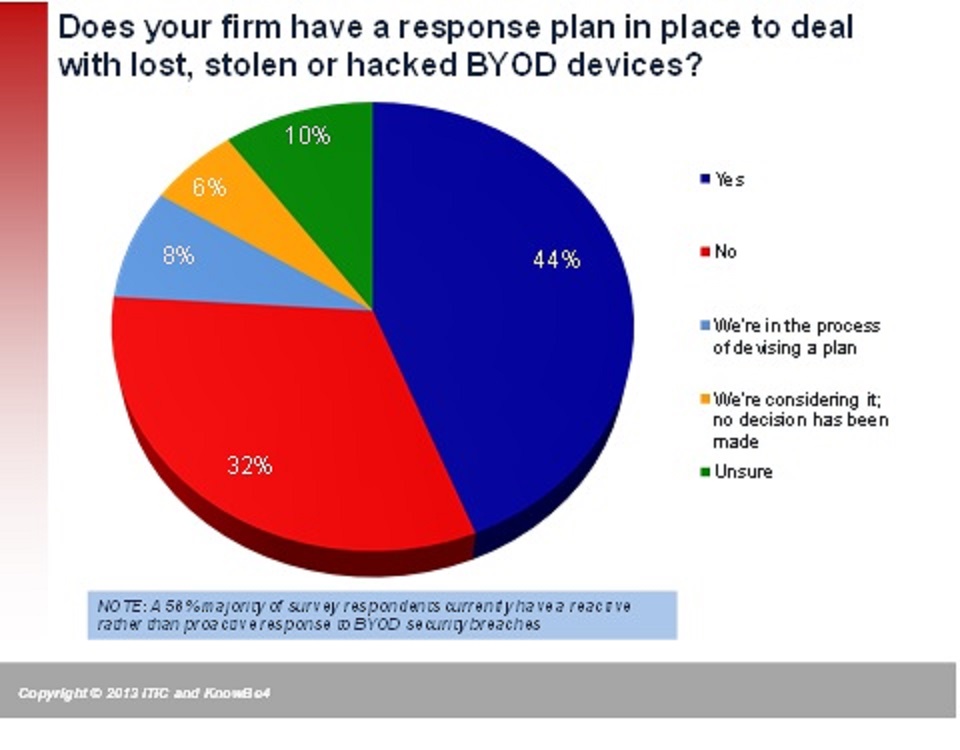
 More than half theorganizations responding to a new survey said they have no responseready for a hack into data on notebooks, tablets and smartphonestheir staff is using as “bring your own devices.”
More than half theorganizations responding to a new survey said they have no responseready for a hack into data on notebooks, tablets and smartphonestheir staff is using as “bring your own devices.”
(Click on the chart at left toexpand.)
|The survey – conducted by Information Technology IntelligenceConsulting and security trainer KnowB4.com – also found that halfof the respondents concede that BYOD and corporate-owned devices may have been breached in thepast 12 months without their knowledge, leaving data andapplications alike vulnerable to internal and external threats.
|ITIC and KnowBe4 said they drew their conclusions from aFebruary survey conducted online among IT professionals at morethan 300 organizations in 30 vertical market segments including 80%from North America and ranging in size from fewer than 200employees to more than 10,000.
|Along with no knowing they had been breached or having a planfor dealing with problems from personal devices, ITIC and KnowBe4said, “56% of organizations acknowledge they are not fortifyingtheir existing security measures, taking extra precautions orimplementing security training despite recent high-profile securityattacks against Fortune 1000 firms like Adobe, Reuters, Target,Skype, Snapchat and others.”
|Other survey highlights:
- Thirty-four percent of the participants acknowledged theyeither “have no way of knowing” or “do not require” end users toinform them of security issues with employee-owned BYOD.
- Three in 10 respondents were unaware or unable to discernwhether BYOD security breaches impacted servers, mission criticalapps or network operations.
- Thirty-two percent said they either have no BYOD-specificsecurity in place or don't know.
“Individually and collectively, the inability of a significantsegment of corporations to track and secure both company andemployee-owned BYOD devices undermines IT and securityadministrators' ability to secure the environment,” the reportsaid.
|“It also creates a larger attack vector for hackers. And itmakes servers and mission critical applications more vulnerable toinfection by rogue code, malware or sensitive data that washijacked when a BYOD device's security was compromised,” itsaid.
|ITIC and KnowBe4 also found that the IT staff they spoke withwere not necessarily happy about it.
|“Anecdotal evidence obtained from first-person customerinterviews indicates that 75% of IT and security managers are nowlobbying executive management to construct BYOD-specific securitypolicies to plug potential vulnerabilities,” the companiessaid.
|Recommendations from the report – titled “2014 State ofCorporate Server, Desktop and BYOD Security Trends Survey” – included:
- Conduct regular security audits and vulnerabilitytesting. Include server hardware, server OS, applicationand network infrastructure to identify vulnerabilities and comparesecurity across platforms.
- Regularly review and update policies andprocedures. Corporations should review and update theirsecurity policies annually at a minimum or as needed to addressemerging technologies and trends like BYOD and mobility.
- Perform due diligence. Become familiar withall specifics of the platform before beginning any new technologydeployment (such as server hardware, application software,virtualization and cloud deployments.)
- Ensure compliance. The ability to adhere tocompliance standards and meet service-level agreements hinges onserver security, reliability and uptime.
- Estimate the cost of downtime. “Being able toaffix a monetary cost to a security breach and assess the potentialrisk and damages that ensue in the wake of a security breach, willmake the most cogent and compelling case for strong securitymechanisms and security awareness training,” ITIC and KnowBe4said.
Complete your profile to continue reading and get FREE access to CUTimes.com, part of your ALM digital membership.
Your access to unlimited CUTimes.com content isn’t changing.
Once you are an ALM digital member, you’ll receive:
- Critical CUTimes.com information including comprehensive product and service provider listings via the Marketplace Directory, CU Careers, resources from industry leaders, webcasts, and breaking news, analysis and more with our informative Newsletters.
- Exclusive discounts on ALM and CU Times events.
- Access to other award-winning ALM websites including Law.com and GlobeSt.com.
Already have an account? Sign In
© 2024 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.









